Security Initiatives
Efforts to provide safe and secure services
As part of its efforts to provide robust services, LY Corporation (the "Company") addresses the vulnerabilities of applications by conducting such measures as vulnerability examinations through dedicated internal organizations and third-party institutions. In addition, it holds secure programming trainings for engineers with the aim of preventing application vulnerabilities. The trainings are positioned among important trainings for both strengthening the abilities of engineers and achieving compliance with international cybersecurity standards, and have been mandated for all engineers in the company.
The services that have been provided by LINE Corporation are operated through the LINE Security Bug Bounty Program, a program that publicly solicits service vulnerability discoveries and pays rewards to those who report them, in order to quickly discover vulnerabilities in LINE messenger app or related websites, and to provide secure service to the users.
Related links
Protection and management system for data of users in Japan
To address the ever-expanding, increasingly sophisticated, and global nature of cybersecurity risks, LY Corporation implements a range of cybersecurity measures, taking into account frameworks such as the Cybersecurity Framework established by the U.S. National Institute of Standards and Technology (NIST), which is widely referenced around the world across all industries.
The following outlines LY Corporation’s key cybersecurity measures based on the NIST Cybersecurity Framework.
The NIST Cybersecurity Framework provides a taxonomy that enables organizations to communicate cybersecurity risks effectively with stakeholders both inside and outside the organization.
It is structured around six functions—such as “Govern,” “Identify,” and “Protect”—and covers a broad spectrum of cybersecurity management strategies, ranging from risk management and preventive measures during normal operations to response and trust-recovery efforts after incidents occur.
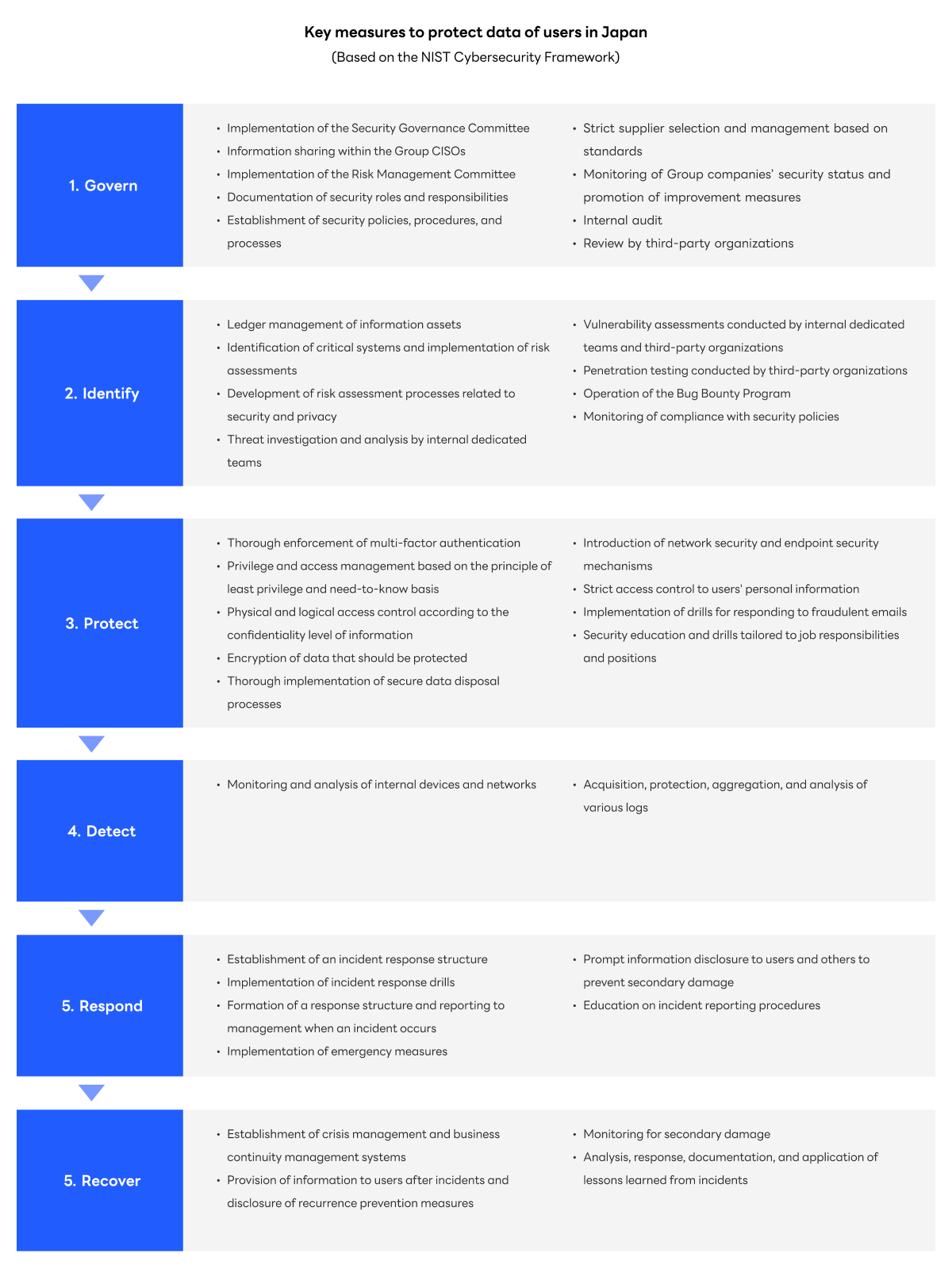
- 1 Govern | Establishing and managing cybersecurity strategies and policies
-
The LY Corporation Group (the “Group”) has formulated the LY Corporation Group's Cybersecurity Policy under which it makes its utmost efforts to address information security threats in accordance with its information security principles of protecting its users from information leaks (confidentiality), providing round-the-clock service (availability), and securely protecting the service contents from destruction or fabrication (integrity).
A Security Governance Committee—chaired by the President and Representative Director and joined by the CISO, CTO, and other security-related corporate officers—is established to discuss improvements to security governance.
To enhance security across the Group, the Group engages in close information sharing and continuous improvement activities through the Group CISO Board.
Furthermore, the Group applies strict criteria to supplier selection and management to strengthen the overall supply chain.
Purchasing and procuremenInternal assessments and third-party audits are conducted to identify gaps between the Group’s current state and relevant domestic and international security standards and frameworks, and to implement necessary improvements.
- 2 Identify | Identification and assessment of assets and risks
-
Critical systems at LY Corporation and the safety management measures required for them have been defined, and a framework to identify and manage risks has been developed and implemented as part of a risk management process based on ISO27001.* Specifically, as part of the annual risk assessment, a framework has been established to comprehensively identify and assess the current state of data storage, the security measures in place, and the associated risks for each system.
Additionally, vulnerability assessments of services and evaluations of the effectiveness of security controls are regularly conducted through collaboration between external expert organizations and internal specialized teams.
Furthermore, the Company operates its Bug Bounty Program, which aims to identify vulnerabilities in systems and services at an early stage with the cooperation of external ethical hackers, and manages a vulnerability reporting form.
* ISO27001: International standard for Information Security Management Systems (ISMS) - 3 Protect | Implementation of measures to protect identified assets
-
Access to the personal information of the Company’s users is strictly governed through rigorous physical and logical access controls, implemented in consideration of potential threats arising from both internal misconduct and external attacks (cyberattacks).
For example, in order to prevent the unauthorized removal of highly confidential user data, a dedicated security area has been established, isolated from the general office environment and governed by specific rules such as prohibitions on bringing in certain items. In addition, access to highly confidential user data from outside the designated area is allowed only under certain conditions, including emergencies, and only with measures such as restricting the data that can be accessed and requiring at least two personnel to be present during the operation. - 4 Detect | Early detection and response to security incidents
-
To detect incidents early and minimize potential damage, external expert organizations and internal specialized teams work together to conduct security monitoring 24 hours a day, 365 days a year.
- 5 Respond | Appropriate response to incidents
-
The Company prepares for rapid and appropriate action in the event of an incident by maintaining incident response standards and structures, and by regularly conducting incident response drills.
When an incident occurs, an accident response structure is quickly assembled, and actions are taken to minimize damage. In addition, depending on the severity of the incident, the impact and response status are promptly reported to top management.
Furthermore, cross-functional teams, including security organizations overseen by the CISO, promptly disclose information to prevent the situation from escalating, bring it under control quickly, and prevent secondary damage. - 6 Recover | Post-incident recovery and communication
-
To quickly restore functions and services affected by large-scale disasters, failures, or cybersecurity incidents, the Company has established crisis management systems and business continuity management systems.
Execution plans and their progress are also confirmed by the Security Governance Committee, chaired by the President and Representative Director, as well as by the Top Management Committee.
System for sharing information with external organizations
In order to keep abreast of new threats to information security, LY Corporation is cooperating with the following organizations and continues to grasp the latest technological trends.
| Organization Name | Collaboration Details |
|---|---|
| Through close collaboration with CSIRT, LY Corporation strives to solve social issues commonly faced by the member companies of CSIRT. | |
| By sharing information on cybercrime, LY Corporation works to identify the roots of threats in cyberspace, reduce and nullify the threats, and prevent future incidents from occurring. | |
| LY Corporation contributes to inter-organizational collaborations during incidents from a technical standpoint. |
Countermeasures against phishing websites and unauthorized use
LY Corporation responds to phishing as part of the incident response related to information security of the companies of the LY Corporation Group. In collaboration with related companies and agencies, phishing is detected at an early stage and unauthorized websites are disabled on an ongoing basis.
To prepare for instances where a third-party gains knowledge of a user's ID or password, LY Corporation conducts countermeasures to prevent fraudulent logins and mitigates damage should such logins occur. At the same time, it works to raise awareness among Japanese Internet users on managing login IDs in a secure manner and has preventive measures in place that anticipate a certain level of improper access.
Related links
Thorough security education and training
LY Corporation provides education and drills tailored to employees’ roles and responsibilities to ensure that users can continue to enjoy safe and secure services.
Additionally, for Group companies, certain security education and drills are conducted jointly so that the entire Group can maintain a consistent and high security standard.
| Training Name | Content |
|---|---|
| Security training for all employees |
Once every quarter, the Company conducts e-learning sessions for all employees to review the basic rules of information security within the company. Ad hoc security training sessions are also conducted as needed. < 2025 implementation status and participation rate > February 2025: 99% March 2025: 99% May 2025: 99% August 2025: 98% |
| Security training for new hires | New graduate and mid-career hires are required to complete e-learning programs that cover general information security knowledge, countermeasures, and the Company's basic information security rules. |
| Security training for newly appointed managers | Employees appointed to managerial positions must undergo e-learning programs to acquire the requisite knowledge for their roles. |
| Security training for engineers |
New employees involved in programming are given training to help them adopt a secure development mindset. After joining the Company, employees also receive annual training to stay updated about the latest security threats and countermeasures. |
| Targeted attack response drill | Training emails simulating targeted email attacks are sent at least once a year to improve employees' incident response capabilities. |
| Incident drill | Assuming the occurrence of information security incidents, annual drills are conducted to rehearse response procedures and verify the effectiveness of the response flows. |
We would like to inform you that we will be temporarily suspending LINE Security Bug Bounty Program starting December 3, 2025, to review and improve the program's content and structure.