Approach to Privacy & Security and Systems
The advancement of information technology has brought about greater convenience and affluence in our lives. Meanwhile, the development of information technology, particularly AI technology, entails the handling of vast amounts of data across national borders, potentially increasing security-related incidents and infringing privacy and other rights and interests. Therefore, there is an increasing need to handle data in an appropriate manner from the perspective of enhancing security and protecting privacy.
Guided by its "Privacy & Security First" management policy, LY Corporation is dedicated to enhancing security and protecting privacy for the safety of its users so that users can use its services with confidence at all times.
In order to realize this management policy, LY Corporation adheres to the following five principles as stipulated in the Basic Policy on Data Protection.
Five principles
- The primary purpose is to provide benefit to our users
- We handle data with an emphasis on transparency
- We endeavor not to infringe on the rights and interests of our users
- Data provided to us belongs to our users
- We protect and manage data under appropriate security management system
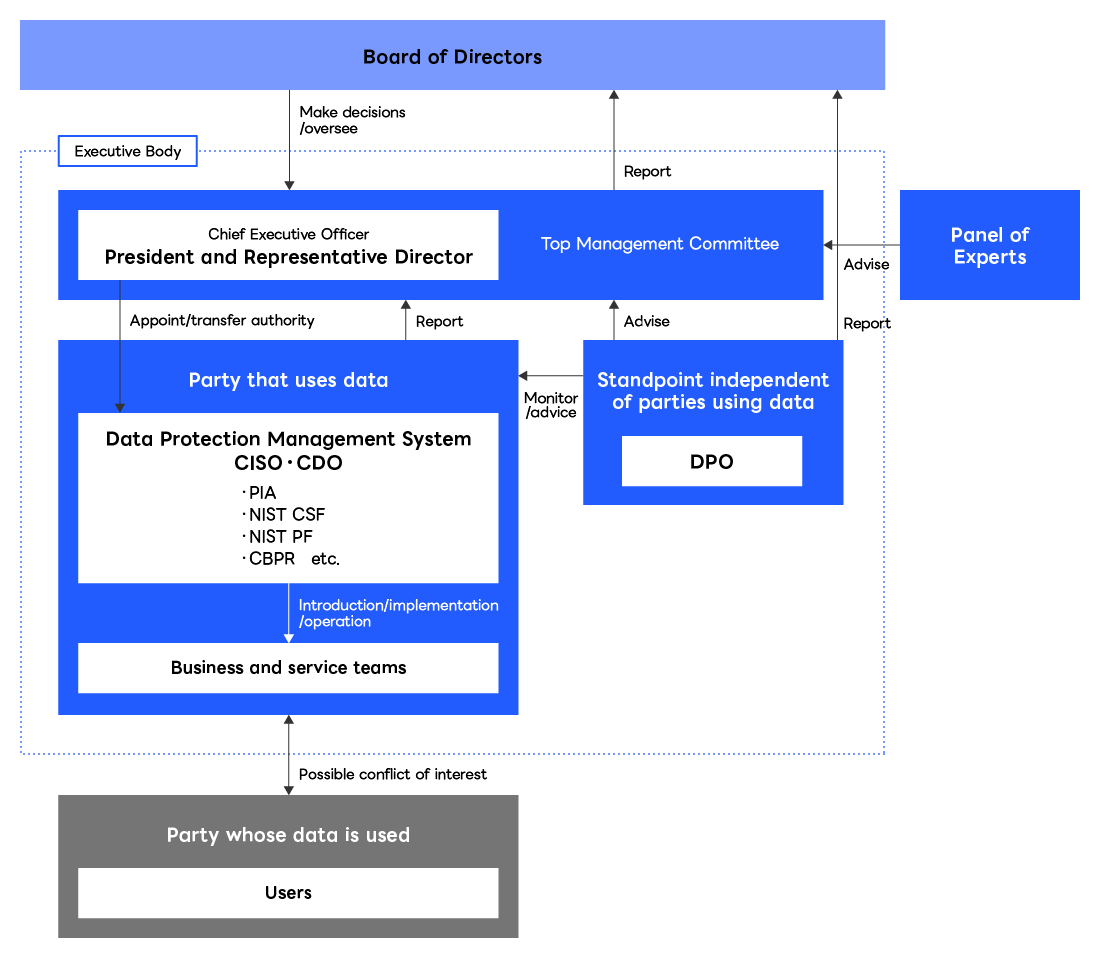
In adhering to these principles, LY Corporation establishes and strengthens its governance system from the users’ perspective and promotes initiatives such as conducting Privacy Impact Assessments (PIA)*1, introducing the Cybersecurity Framework and Privacy Framework defined by the U.S. National Institute of Standards and Technology (NIST)*2, and acquiring certification from the APEC Cross Border Privacy Rules (CBPR)*3 System. Similar initiatives are also promoted at Group companies. In addition, from before, LY Corporation has made its best efforts to address information security threats with the following policies: protect customers' information from leakage (confidentiality), continue to provide services to customers 24/7 (availability), and ensure that contents are protected from destruction or tampering (integrity).
In order to ensure compliance with these principles, an internal structure is in place that includes a Chief Data Officer (CDO) who oversees the Company’s data domain and a Chief Information Security Officer (CISO) who supervises the Company’s information security and cybersecurity domain. These officers are responsible for strengthening security and protecting privacy in their respective areas.
In an effort to ensure that the use of data does not violate the five principles, the Company also appoints a Data Protection Officer (DPO) to monitor the use of data from an independent third-party standpoint within the Company and to provide advice from the user's perspective.
LY Corporation ensures that the above series of efforts will continue to be improved through regular feedback by an expert panel composed mainly of external experts.
Transparency reports will also be published periodically to report on how the Company has handled some of the data entrusted by its users.
*1 PIA refers to a preliminary assessment process to confirm that the systems, services, and features provided by the company adequately and sufficiently consider the impact on privacy and other rights and interests.
*2 LY Corporation has introduced a maturity assessment of its data protection management system based on the NIST Cybersecurity Framework and Privacy Framework defined by NIST.
*3 CBPR refers to an international certification system that verifies whether the company complies with the APEC Privacy Principles, a set of rules that adequately protect data transferred across borders.
In addition to the appointment of a DPO within the Company, LY Corporation also requires the appointment of DPOs at major subsidiaries and affiliates that handle data entrusted by users, and promotes the initiatives described above while providing the necessary support.
The Company will strengthen the data governance of the entire Group by establishing an autonomous governance system that is in line with the business of the Group companies, and a Group-wide governance system that is centralized and compatible with the global business operating environment.